SSL VPNs (Secure Socket Layer Virtual Private Networks)
Security is key when accessing remote devices. The basics, such as changing default passwords, locking down ports and switching off unnecessary services, are all good practices for locally securing a device. A system must nevertheless deal with outside efforts that may disrupt data transmission, or in the worst case, destroy it.
A few methods of transportation are available for remote communication. It can be over public or private infrastructure, with encryption playing a crucial role in both. One way to isolate access to external threats is to set up a private infrastructure using either cellular or fixed-line technology. Essentially, the network will operate like the Internet, but will only be available to a specific customer. This can allow interconnectivity between a top-end system and remote devices, with the addition of privacy. Despite this, the information transmitted between these locations is not encrypted or secure.
The Internet is also a very suitable method of communication over public infrastructure. One of the biggest challenges is that transmission between the top end and remote sites will not be private. With the right tools, anyone can monitor and observe traffic. This is why you should always use encryption and a virtual private network (VPN).
There is no preference for using either the public or private networks. Public Networks, such as the Internet, have billions of secure communications between sites in existence.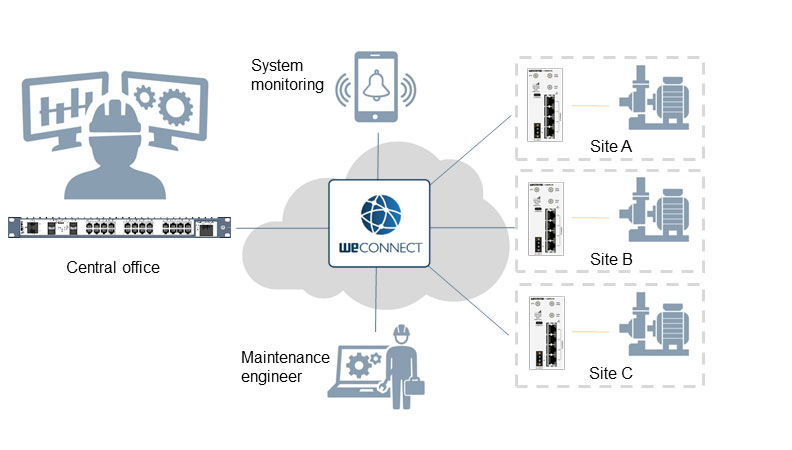
The use of VPNs and protocols such as Secure Socket Layer (SSL) makes communication more secure. Certificates are used in SSL to ensure trust between Site A & Site B. The trust is based on public and private keys, where the public key is shared, but the private key is not. The public and private keys are verified regularly on each device, to ensure their validity within the infrastructure. WeConnect is an example of SSL encryption which is used on many mission-critical networks in industries such as Oil & Gas, Shipping, Power, Water & Wastewater and Aviation.
Managing the certificates requires a trusted authority. One of the biggest advantages of SSL is the ability to distribute and revoke certificates. The certificates will be updated periodically to ensure the network is secure and communication is uninterrupted. When an authority notices suspicious activity, they can revoke the certificate, making it invalid and issuing a new one. Using this method, data can be transported securely over a public network, such as the Internet. As a result, Site A and Site B remain operational.
When it comes to public networks, SSL VPNS offer an additional layer of security to ensure your system is safe. Considering private networks are private, "over the air" encryption or IPSec VPNs can provide an added layer of security to your network. Regardless of the type of network and method you choose, Westermo has the expertise and technology to support you every step of the way.

Featured product
The robust and compact Merlin 4400 cellular router is the ideal fit for utility and industrial applications. Featuring zero-touch large-scale deployment and comprehensive cybersecurity capabilities, such as secure boot and TPM (Trusted Platform Module).
Learn more
Cloud based networks
System administrators and engineers can access the system from the comfort of their homes to manage, monitor and support remote sites.

On premise router connectivity
Remote locations, even if they are sometimes in undesirable areas, can now be brought on to the network for greater visibility.

SSL VPNs
The use of VPNs and protocols such as Secure Socket Layer (SSL) makes remote communication more secure.

Remote diagnostics and support
System administrators and engineers can access the system from the comfort of their homes to carry out diagnostics and support.
Explorez toutes les solutions d'accès à distance
Depuis des décennies, nous proposons des produits et des solutions pour les applications de réseaux d'accès à distance. Grâce à notre vaste gamme de produits et à notre connaissance approfondie des applications, nous sommes en mesure de proposer la meilleure solution pour vos besoins.

Accès à distance pour les applications utilitaires
La connectivité cellulaire permet de surveiller les sites de manière globale.

Accès distant pour les applications industrielles
Obtenez une vue d'ensemble des sites qui étaient autrefois habités ou relativement invisibles.

Cyber-sécurisation des réseaux distants
Il n'a jamais été aussi important de garantir la sécurité de vos réseaux et systèmes industriels distants.

Réseaux Zero Touch
Déployer et assurer la maintenance de milliers de routeurs de manière rentable.

Conversion de protocole
La conversion de protocole permet de transmettre ou de recevoir un flux commun de données vers le SCADA Supérieur.

Remplacement du modem existant
Faites migrer les anciens dispositifs série des communications par modem commuté ou ligne louée vers la série sur IP à large bande.
Carl de Bruin
International sales

Pour toute requête technique, merci de vous orienter vers le contact support
